Account takeover (ATO) fraud attacks were once large-scale, “scattershot” campaigns. In recent years, however, they have morphed into smaller, more finely-tuned attacks. As a result, they are significantly more effective. Here’s what you need to know to fight back and protect your business.
The Rising Cost of ATO Fraud
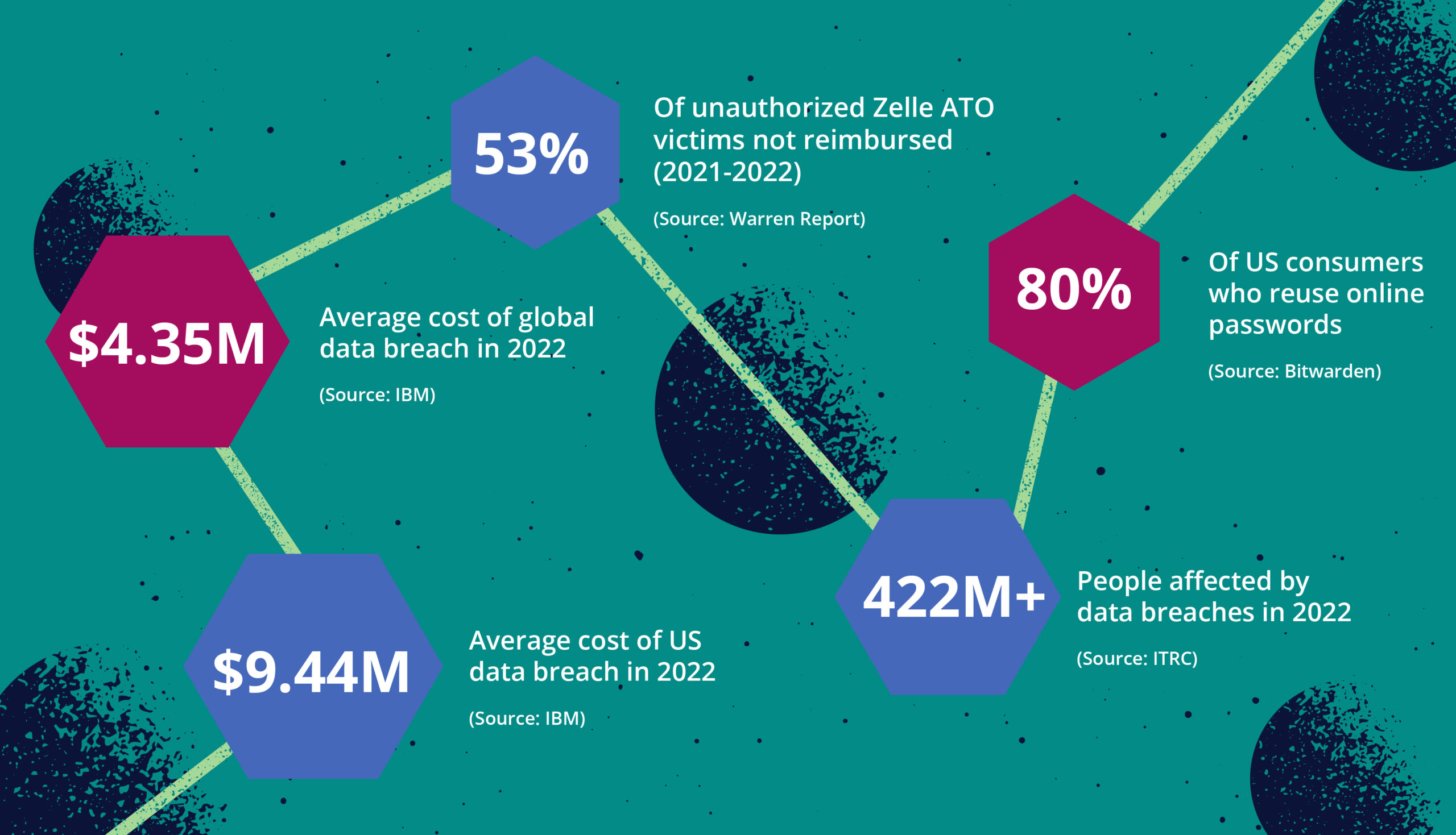
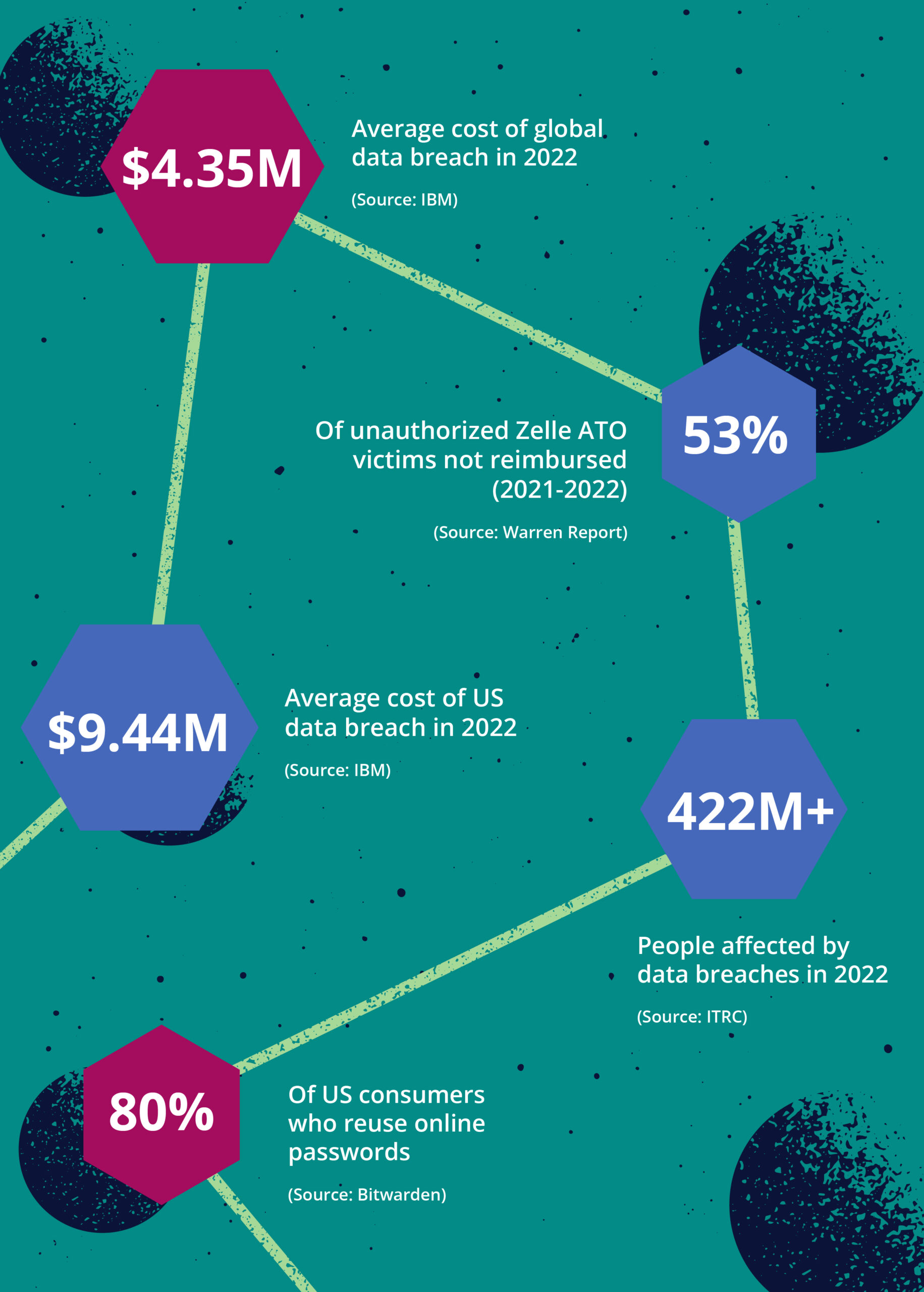
Fueled by societal and economic instability, fraudsters utilize fraud-as-a-service social engineering sites and easily obtain malware to commit identity theft and access customer accounts (i.e., phishing attacks, stolen account credentials, remote access trojans (RATs)). The costs of these attacks can be substantial. Recent data indicates the global average cost of a data breach reached $4.35 million in 2022. In the United States, the average cost of a data breach is $9.44 million – more than twice as high as the global average.
It’s no secret that fraud is a constant game of cat and mouse: bad actors develop new attack techniques and utilize the latest credential-stuffing automation technology while banks upgrade their capabilities in response to keep pace. But why is the cost of ATO rising so rapidly?
2 Key Reasons Why Account Takeover Fraud is Rising
There is a two-part answer to this question. First, the expansion of new payment methods and increased speed of payment transactions over the past decade enables fraudsters to rapidly scale their operations and profit faster from their scams.
Peer-to-peer (P2P) payment applications have steadily increased among consumers in the U.S. As these P2P apps have been developed and rolled out, they’ve been key targets for fraudsters to exploit. The P2P platform Zelle, for example, recently marked its 5-year anniversary by logging $1.5 trillion in transactions since its 2017 inception. While Early Warning Services, the company that operates the Zelle network claims 99.9% of these transactions are fraud- and scam-free, a report by a US lawmaker claims otherwise. The report by Sen. Elizabeth Warren (D-MA) found banks only reimbursed 47% of the dollar value to consumers who claimed they experienced unauthorized payments on Zelle in 2021 and the first half of 2022.
Second, fraudsters realize that banks are often slow to determine whether an ATO attack is in progress and stop it before the fraud is committed. Current ATO solutions focus on detection and alerts, placing the remediation burden on the bank’s transaction monitoring system to stop fraud. This gives fraudsters a window of opportunity to commit account takeover fraud before a bank responds.
Recovering the money exfiltrated via these new digital channels is extremely difficult, which further contributes to the growth of ATO fraud. Combine that fact with the rapid growth of anonymous payment methods (e.g., different types of cryptocurrency), and fraudsters have several ways to move money quickly out of accounts.
How Fraudsters Pull Off ATO Fraud Attacks
With the above method of exfiltrating funds, ATO attacks become even more widespread thanks to the availability of personal information compromised through data breaches. A recent report recorded 1,802 data breaches in 2022 affecting over 422 million victims. Interestingly, this figure is just 60 data breaches short of the 2021 record.
This stolen information opens the door to a range of ATO techniques for bad actors. Data breaches and proactive means of stealing credentials such as phishing and its variations (smishing, vishing, etc.) have led to a wide range of consumer data available for purchase on the dark web. These arms would-be fraudsters with the tools they need to convincingly pretend to be legitimate customers.
According to at least one report, more than 80% of Americans reuse their passwords for multiple websites. As more and more bank account credentials are compromised and bought and sold on the dark web, fraudsters can successfully use each set of credentials on both the compromised account and other businesses that use the same email address or phone number.
Other advanced methods of compromising information include ID-stealing malware, where targeted malicious code is designed to swipe banking credentials. Stolen credentials enable fraudsters to use legitimate credentials to break into a customer’s account, change contact information to receive alerts and one-time passcodes (OTPs), and drain the account of funds. Some bad actors use a class of malware called remote access tools or trojans (RATs) designed to hijack a customer’s banking session or transaction after the legitimate user has already logged in.
With the confluence of new digital payment technologies, the ease for fraudsters to move money and the struggle for banks to recover it, and the dramatic increase in availability and quality of breached records, how can banks can stay ahead?
3 Steps to Prevent ATO Fraud
Fraudsters are innovative and know how to make the modernization of payment technology work in their favor. The best way for banks to protect their customers from the ATO fraud threat is to embrace a strategy of prevention. This strategy rests on three core principles.
1. Know Your Users
The key to fighting fraud is verifying without a doubt that each customer is who they claim to be and is not being impersonated or manipulated at any point in their online journey.
Behavioral biometric analysis has become the cornerstone of any comprehensive online fraud prevention strategy, as it allows FIs to both know their user and verify their identity at every interaction and create a holistic digital identity. It works by analyzing hundreds of parameters that make up a user’s typical online behavior, such as the way they type their name, how they access their online accounts, the pressure they apply to their screen, or the rhythm and cadence with which they type. Combining the user’s device usage information with device intelligence, network assessment, malware detection, and other contextual data enables FIs to create a digital identity unique to each user.
Another key benefit of a solution employing this kind of analysis is that it occurs silently, behind the scenes, enabling FIs to give their customers frictionless protection and block bad actors while simultaneously speeding up the process for legitimate users.
2. Take a Proactive Approach
Solution-based detection for malware is simply no longer effective. By the time malware is detected, it is already too late. In other words, the missile must be destroyed before striking its target.
Instead, robust protection requires an always-on fraud response. To keep up, FIs must find a solution that employs an active defense and blocks potential fraud in real time. Active defense capabilities prevent malware from successfully manipulating a user into taking action that compromises a session or from stealing credentials. This reduces the number of alerts sent to the internal fraud team and paves the way for a preemptive defense. FIs can use link analysis to discover bad actors and mule accounts tied to fraudulent behavior hiding in their system and stop them at the point of discovery.
3. Protect the Payment Process
An ideal fraud prevention solution should block bad actors from reaching the point of transaction. A proactive approach to blocking ATOs and preventing complex attacks makes it extraordinarily challenging and expensive for cybercriminals to ever get to that stage.
To accurately assess the risk of transaction fraud, FIs must treat each customer as a unique individual. Machine learning models can establish a baseline of typical behavior and continually learn an individual’s transactional patterns, frequency, amount, and more — at scale. This granular level of analysis identifies suspicious anomalies based on historical patterns and creates more meaningful alerts. This approach also helps mitigate false positives and negatives and avoids making online processes complex and challenging for genuine users attempting to carry out their regular transactions.
Fraudsters are always innovating, have more opportunities than ever before, and understand how easy it is to profit from account takeover fraud. Embracing a strategy of prevention is the most important step any bank can take to protect their customers and bottom line.
Share this article:
Related Posts
0 Comments6 Minutes
A Guide to Secure, Seamless User Authentication in Payments
Online payments demand a delicate balance between security and user experience. Consumers…
0 Comments7 Minutes
Combating Emerging Scams in the Philippines
The Philippines is witnessing remarkable growth in digital banking. Unfortunately, a…
0 Comments5 Minutes
Feedzai is a Leader in the 2024 IDC MarketScape for Enterprise Fraud Solutions
Exciting news! Feedzai, the world’s first RiskOps platform, is proud to have been named a…


