Fraud is a global problem. Some fraud types are more likely to originate from specific geographies than others. In the first of this two-part post, we share some of the most troublesome global fraud hot spots and the common types of fraud that originate from these locations.
Tune in next week to learn what financial institutions (FIs) can do to protect their customers, regardless of where fraud occurs.
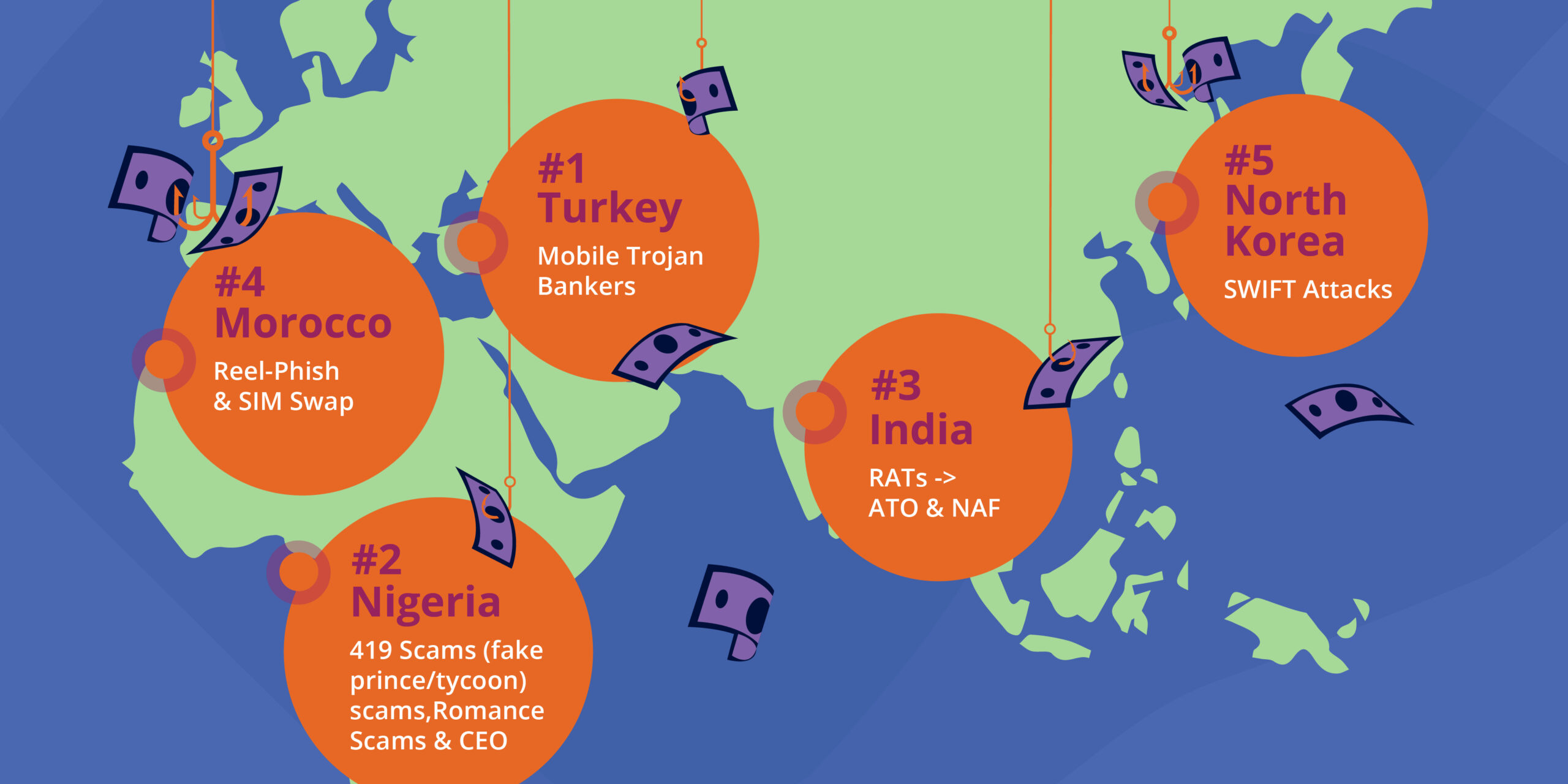
The Top 5 Global Fraud Hot Spots
1. Turkey
Highly sophisticated mobile trojan banking malware has become increasingly common among fraudsters worldwide – and Turkey is currently leading its usage. This malware includes many of the same features as earlier banking trojan variants. These include SMS grabbers, which spy on text messages like one-time passcodes (OTPs) and screen overlays, which enable fraudsters to duplicate a trusted login portal and steal personal information like usernames and passwords.
What makes this mobile trojan banking malware popular with bad actors? It offers on-device fraud (ODF) and integration with automated transfer systems – a malware-as-a-service feature that enables criminals to move money using APIs. In practice, this means bad actors can use the APIs to connect with more “suitable” money mules that can more easily avoid detection.
Frequent targets: Turkish-based bad actors are most frequently targeting their country. Outside of Turkey, targets include Spain, Poland, Australia, USA, UK, Germany, Italy, and many more.
2. Nigeria
Nigeria was a pioneer in starting many internet and telecommunication-based scams. However, these internet-based scams have evolved and today are being executed in multiple countries.
- 419 Scams: This scam has been around for years but has evolved over time. Fraudsters send a letter, email, or fax to a target pretending to be a wealthy individual (e.g., a deposed royal family member, businessman, or military officer). They ask their target to give them access to their bank account to help them move their (fake) fortune out of Nigeria. If they are successful, victims will share their account information and may even send their own money to help cover the costs of moving the imaginary fortune.
- Romance Scams: Nigeria is also a hot spot for romance scams. Fraudsters find people online looking for a romantic connection and pretend to be romantically interested. Then, they pressure or manipulate their target into sending them money for travel or for medical expenses.
- CEO Fraud: In CEO fraud, fraudsters email a company employee pretending to be the organization’s CEO or another high-level executive. They’ll give the employee an urgent request to send money to an account they control. This type of fraud often relies on business email compromise (BEC).
Frequent targets: These scams are common in the USA and UK. The pandemic has given strong momentum to romance scams in particular worldwide.
3. India
In India, it’s common to find organized fraudulent services – sometimes known as “farms” – that operate in the black market. It’s also common for fraudsters operating from these farms to use tech support scams to access a target’s account. Fraudsters will call a victim pretending to offer technical assistance and persuade the target to give them remote access to their device. Once they gain access, the fraudster will either plant a remote access trojan or remote access tool (RAT) onto the device.
Once the RATs are installed, fraudsters can use their victims’ stolen credentials to commit account takeover (ATO) and new account fraud (NAF).
- Account Takeover: Account takeover fraud can take on many forms and rely on different tactics. In the case of India, This enables them to either hijack a user’s existing session or access their device remotely without their victim realizing it.
- New Account Fraud: In the case of NAF, fraudsters will use a target’s stolen account information to create a new account with a financial institution. In some cases, fraudsters recruit money mules to onboard with banks. Once they onboard, they can apply for loans or credit cards and max out their credit before disappearing.
Frequent targets: Targets frequently are based in the USA and UK, but almost any country can be affected by these scams.
4. Morocco
ReelPhish attacks among the most common types of fraud originating in Morocco. ReelPhishing works by enabling fraudsters to bypass two-factor authentication (2FA) methods – and in real-time. First, it presents targets with a phishing site that mimics a legitimate website. Believing the site to be legitimate, the user enters their online username and password. It then opens a new (fake) website for the user to enter their one-time password (OTP). At this time, the attacker can steal their target’s username, password, and OTP to access their online account.
Fraudsters based in Morocco also rely on SIM Swap fraud – in which fraudsters manage to transfer a legitimate customer’s phone number to a different device they control. Vishing swaps are another common tactic in which fraudsters target employees at telecom companies to trick (or bribe) them into gaining access to users’ voicemails and phone calls.
Frequent targets: Morocco-based fraudsters often focus on southern European, Middle Eastern, and Latin America-based targets.
5. North Korea
North Korea is an outlier in this group because many of its worst types of fraud are state-sponsored attacks. The North Korean government operates a group of hackers known as the Advanced Persistent Threat 38 (APT38), linked to attacks on the US film industry in 2014 over the controversial film “The Interview.”
APT38 has also been linked to numerous financial crimes across Asia and Africa. These include an attack on the SWIFT financial messaging network that resulted in the theft of roughly $100 million from banks in the US, Mexico, Poland, Vietnam, Bangladesh, Turkey, and many other nations. Along with other stack-backed hacking groups, the group is also linked to ATM cash-out attacks in Pakistan.
North Korea is heavily sanctioned by the global community. As a result, it has turned to multiple cybercrimes as a revenue stream. These crimes include hacking cryptocurrency and launching cyberattacks on US military and critical infrastructure targets over its role in the Ukraine-Russia conflict.
Frequent targets: North Korean actors frequently target US-based industries (banking, film, finance, cryptocurrency, and infrastructure). Other top targets include South Korea, Japan, and top NATO allies.
Just because the fraud hot spot countries listed here are known for these specific tactics does not mean that these same fraud techniques don’t originate from other countries as well. Nor does it mean that other types of fraud don’t originate from the hot spot nations listed here.
Regardless of where fraud originates, banks and financial institutions need to be prepared to stop it before it can do any damage to customers. Watch this space to learn what banks and financial institutions can do to stop fraud before it can do any harm to customers.
Download The APAC Bank’s Guide to Building Digital Trust to understand the importance of digital trust and how it will impact FIs across the APAC region.
Share this article:
Related Posts
0 Comments6 Minutes
A Guide to Secure, Seamless User Authentication in Payments
Online payments demand a delicate balance between security and user experience. Consumers…
0 Comments7 Minutes
Combating Emerging Scams in the Philippines
The Philippines is witnessing remarkable growth in digital banking. Unfortunately, a…
0 Comments5 Minutes
Feedzai is a Leader in the 2024 IDC MarketScape for Enterprise Fraud Solutions
Exciting news! Feedzai, the world’s first RiskOps platform, is proud to have been named a…